Exploit
Personalize This
Get insights for your role
Exploit is the second of TOC's Five Focusing Steps—maximizing output from the constraint using existing resources before investing in capacity.
Definition
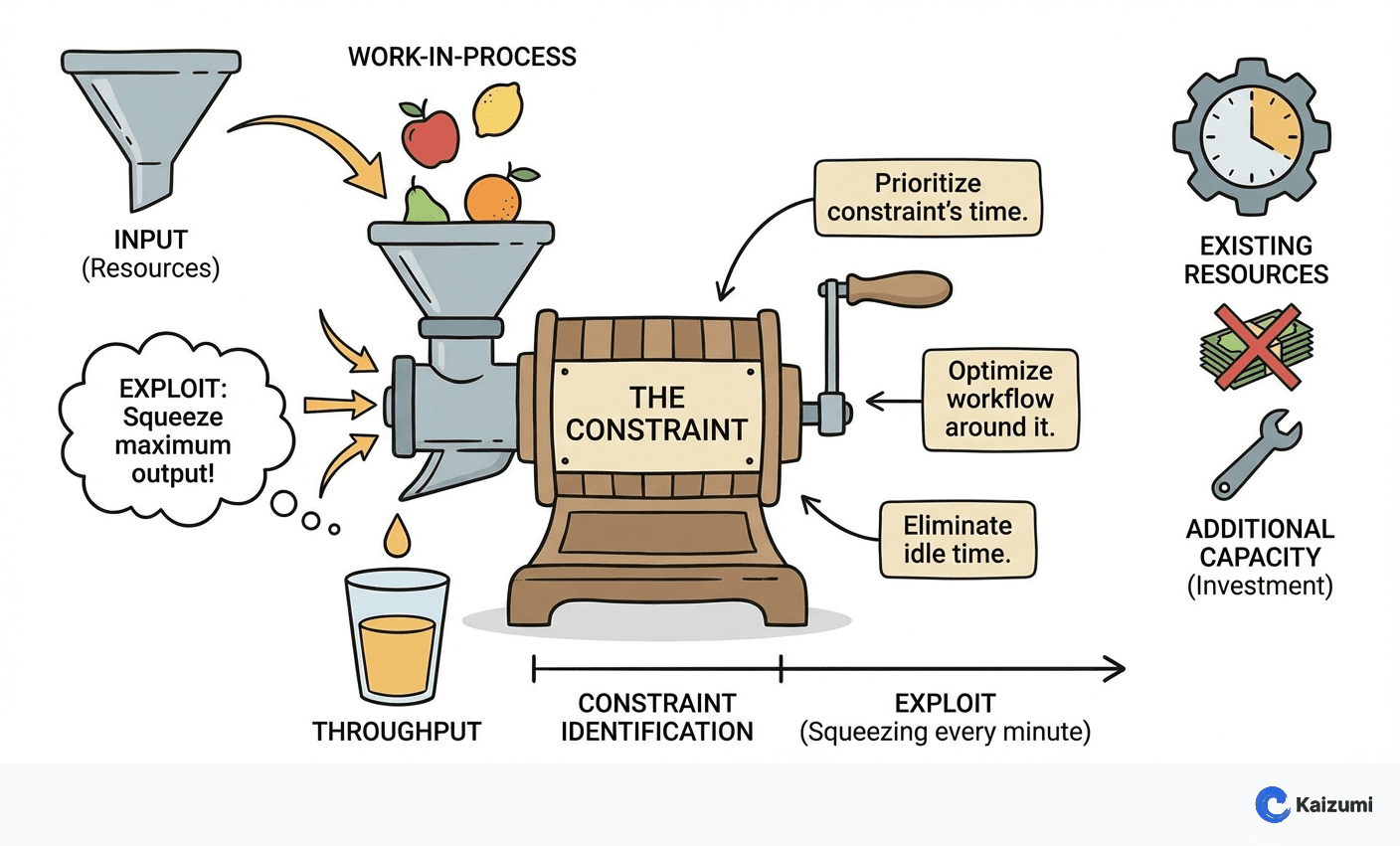
Exploit is the second step in TOC's Five Focusing Steps, following constraint identification. To exploit means squeezing maximum output from the constraint using existing resources—before investing in additional capacity. Since the constraint limits system throughput, every minute of constraint time lost is system throughput lost forever. Exploitation tactics include eliminating constraint downtime, reducing setup time, ensuring the constraint always has work, improving constraint yield, and offloading non-value tasks to non-constraints.
Examples
The constraint machine ran one shift with 30-minute lunch break. Exploitation: staggered operator lunches so the machine never stopped; moved quality inspection from constraint to downstream non-constraint; reduced changeover time 50%. Result: 25% more constraint output with zero capital investment.
Key Points
- Second of Five Focusing Steps—comes after Identify
- Maximize constraint output before investing in additional capacity
- Every minute of constraint time lost is throughput lost forever
- Typical tactics: reduce downtime, offload non-essential tasks, improve yield
Common Misconceptions
Exploit means working people harder. Exploitation focuses on removing waste from constraint operations—not increasing intensity. Often exploitation means removing burdens, simplifying tasks, and providing better support so constraint work becomes easier.
We've already optimized our constraint. Most constraints are 20-50% underutilized. Detailed analysis typically reveals significant improvement opportunity: setup time, waiting, rework, administrative burden, downtime. True exploitation requires systematic analysis.